Application Layer
The application layer is a layer in the Open Systems Interconnection Model (OSI Model) seven-layer model and in the TCP/IP protocol suite. It consists of protocols that focus on process-to-process communication across an IP Network and provides a firm communication interface and end-user services.
An application layer is an abstraction layer that specifies the shared communications protocols and interface methods used by hosts in a communications network. The application layer abstraction is used in both of the standard models of computer networking: the Internet Protocol Suite (TCP/IP) and the OSI model. Although both models use the same term for their respective highest-level layers, the detailed definitions and purposes are different. In TCP/IP, the application layer contains the communications protocols and interface methods used in process-to-process communications across an Internet Protocol (IP) computer network. The application layer only standardizes communication and depends upon the underlying transport layer protocols to establish host-to-host data transfer channels and manage the data exchange in a Client Server Architecture or Peer-to-Peer Architecture (P2P Architecture) networking model. Though the TCP/IP application layer does not describe specific rules or data formats that applications must consider when communicating, the original specification (in RFC 1123) does rely on and recommend the robustness principle for application design. In the OSI model, the definition of the application layer is narrower in scope. The OSI model defines the application layer as the user interface responsible for displaying received information to the user. In contrast, the Internet Protocol Suite does not concern itself with such detail. OSI also explicitly distinguishes additional functionality below the application layer, but above the transport layer at two additional levels: the session layer, and the presentation layer. OSI specifies a strict modular separation of functionality at these layers and provides protocol implementations for each layer. [2]
Application Layer Protocols [3]
- TELNET: Telnet stands for the telephone network. It helps in terminal emulation. It allows the Telnet client to access the resources of Telnet server. It is used for managing the files on the internet. It is used for the initial setup of devices like switches. Telnet command is a command that uses the Telnet protocol to communicate with a remote device or system.
- FTP: FTP stands for file transfer protocol. It is the protocol that actually lets us transfer files. It can facilitate this between any two machines using it. But FTP is not just a protocol but it is also a program.FTP promotes sharing of files via remote computers with reliable and efficient data transfer
- TFTP: The Trivial File Transfer Protocol (TFTP) is the stripped-down, stock version of FTP, but it’s the protocol of choice if you know exactly what you want and where to find it. It’s a technology for transferring files between network devices and is a simplified version of FTP
- NFS: It stands for the network file system. It allows remote hosts to mount file systems over a network and interact with those file systems as though they are mounted locally. This enables system administrators to consolidate resources onto centralized servers on the network.
- SMTP: It stands for Simple Mail Transfer Protocol. It is a part of the TCP/IP protocol. Using a process called “store and forward,” SMTP moves your email on and across networks. It works closely with something called the Mail Transfer Agent (MTA) to send your communication to the right computer and email inbox.
- LPD: It stands for Line Printer Daemon. It is designed for printer sharing. It is the part that receives and processes the request. A “daemon” is a server or agent.
- X window: It defines a protocol for the writing of graphical user interface–based client/server applications. The idea is to allow a program, called a client, to run on one computer. It is primarily used in networks of interconnected mainframes.
- SNMP: It stands for Simple Network Management Protocol. It gathers data by polling the devices on the network from a management station at fixed or random intervals, requiring them to disclose certain information. It is a way that servers can share information about their current state, and also a channel through which an administrator can modify pre-defined values.
- DNS: It stands for Domain Name Service. Every time you use a domain name, therefore, a DNS service must translate the name into the corresponding IP address. For example, the domain name www.abc.com might translate to 198.105.232.4.
- DHCP: It stands for Dynamic Host Configuration Protocol (DHCP). It gives IP addresses to hosts. There is a lot of information a DHCP server can provide to a host when the host is registering for an IP address with the DHCP server.
Functions of Application Layer [4]
- Mail Services: This layer provides the basis for E-mail forwarding and storage.
- Network Virtual Terminal: It allows a user to log on to a remote host. The application creates software emulation of a terminal at the remote host. User’s computer talks to the software terminal which in turn talks to the host and vice versa. Then the remote host believes it is communicating with one of its own terminals and allows the user to log on.
- Directory Services: This layer provides access to global information about various services.
- File Transfer, Access and Management (FTAM): It is a standard mechanism to access files and manages them. Users can access files on a remote computer and manage them. They can also retrieve files from a remote computer.
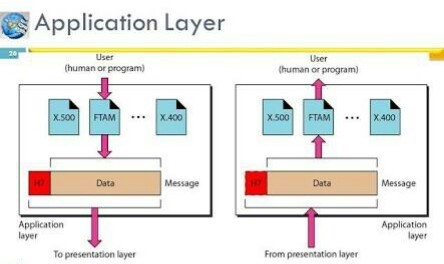
source: Amit Dangarh
Application Layer Threats [5]
The open-ended nature of the Application Layer may present threats. Some of the threats can be summarized as follows:
- One of the prime threats at the Application Layer is poor or nonexistent security design of the basic function of an application.
- Some applications may insecurely handle sensitive information by placing it in publicly accessible files or encoding it in “hidden” areas that are trivially displayed, such as in the HTML code of a web form.
- Programs may have well-known backdoors or shortcuts that bypass otherwise secure controls and provide unauthorized access.
- Applications with weak or no authentication are prime targets for unauthorized use and abuse over the network.
- The TFTP protocol is extensively used for booting of diskless workstations and network device management but does not require any sort of username or password authentication to use its file access ability, giving an intruder possible access to configuration and access information without challenge other than the need to guess filenames.
- Applications may rely upon untrustworthy channels to establish identity or set privilege.
- Overly complex access controls may seem to protect access but fail to prevent unauthorized activity due to poorly understood or written access rules.
Providing Security at the Application Layer [6]
The following steps have been in practice to make the application layer safer.
- Use methods from applications: From the higher levels outside of the model, user input is a significant threat from both deliberate and accidental standpoints. Users may provide unexpected input into the application environment, which if not handled properly could lead to crashes or other unexpected behavior. The unsuspecting hapless user may cause his application to crash or otherwise fail. A malicious user may be able to use bugs and program flaws to attack and gain access to resources or data. Some of the most prevalent controls at the application layer relate to strong design practices in application design and implementation. Applications should make use of the secure facilities available to them in the lower network layers, carefully check incoming and outgoing data, and assume that communications can and will be subject to attack, requiring the use of strong authentication and encryption to validate and protect data as it travels across the network. Applications should also implement their own security controls, allowing for fine-grained control of privilege to access resources and data, ideally using a mechanism that is straightforward and strikes a balance between usability and effectiveness. Detailed logging and audit capability should be standard features of any application that handles sensitive or valuable data. Testing and review are also critical as a control for the application layer. Given the wide variety of both problems and solutions, standards and practices will not be able to capture all possible twists and turns in the application environment. Developers will often have conflicting motivations and agendas regarding their applications, and in a structured programming environment, mandated code security review and application security testing are critical parts of a secure Software Development Life Cycle (SDLC).
- Use hardware security: On the hardware front, Intrusion Detection Systems (IDS) can observe data traffic for known profiles of network activity that can indicate probes for vulnerable applications or an imminent or ongoing attack, as well as detect the presence of undesirable application traffic. Many current host-based firewall systems also include the means to control the access of applications to the network. This control is useful in preventing the unauthorized or covert use of network resources by local programs, as well as providing the conventional layer three and four control functions of a firewall. Many also include basic IDS functionality as well.
- Role of radius protocol: Authentication, Authorization, and Accounting (AAA) protocols such as TACACS [TACACS] and RADIUS [RADIUS] were initially deployed to provide dial-up PPP [PPP] and terminal server access. Over time, with the growth of the Internet and the introduction of new access technologies, including wireless, DSL, Mobile IP, and Ethernet, routers and network access servers (NAS) have increased in complexity and density, putting new demands on AAA protocols. RADIUS provides the following advantages:
- Tight security: RADIUS allows user information to be stored on one host, minimizing the risk of security loopholes.
- Flexibility: Using modifiable "stubs," RADIUS can be adapted to work with existing security systems and protocols.
- The RADIUS server may be adapted to your network, rather than adjusting your network to work with RADIUS.
- Simplified management: Security information is stored in text files at a central location, the RADIUS server. Adding new users to the database or modifying existing user information can be easily accomplished by editing these text files.
- Extensive logging capabilities: RADIUS provides extensive audit trail capabilities, referred to as RADIUS accounting. Information collected in a log file can be analyzed for security purposes, or used for billing.
See Also
The Application Layer is the top layer in both the OSI (Open Systems Interconnection) model and the TCP/IP (Transmission Control Protocol/Internet Protocol) model of computer networking. It provides a set of interfaces for applications to access network services and defines protocols that applications use to communicate over a network. The Application Layer enables user applications to interact with the network, facilitating tasks such as email exchange, file transfers, and web browsing.
- Hypertext Transfer Protocol (HTTP): A foundational protocol used by the World Wide Web, enabling web browsers and servers to communicate. It is a primary protocol of the Application Layer used to request and serve web content.
- File Transfer Protocol (FTP): A protocol used to transfer files between computers on a network. FTP allows users to upload, download, and navigate through files and directories on remote servers.
- Simple Mail Transfer Protocol (SMTP): The standard protocol for email transmission across the Internet. SMTP sends messages from a client to a server and between servers to forward emails to their destination.
- Post Office Protocol (POP) and Internet Message Access Protocol (IMAP): Protocols used by email clients to retrieve emails from a server. While POP downloads email to a local device and typically deletes it from the server, IMAP allows users to view and manage emails directly on the server, facilitating access from multiple devices.
- Domain Name System (DNS): A hierarchical and decentralized naming system used to resolve human-readable domain names (like www.example.com) into machine-readable IP addresses. DNS is crucial for the internet's functionality.
- Dynamic Host Configuration Protocol (DHCP): A network management protocol used to dynamically assign IP addresses and other network configuration parameters to devices on a network, enabling them to communicate with other IP networks.
- Telnet and Secure Shell (SSH): Protocols for remote login sessions over the network. Telnet is an older, unsecured protocol, while SSH provides a secure channel over an unsecured network in a client-server architecture.
- Representational State Transfer (REST) and Simple Object Access Protocol (SOAP) are architectural styles and protocols used for designing networked applications. REST is used in web services and utilizes HTTP for communication, while SOAP is a protocol specification for exchanging structured information in web services operations.
- Session Initiation Protocol (SIP): A signaling protocol used for initiating, maintaining, modifying, and terminating real-time sessions that involve video, voice, messaging, and other communications applications and services between two or more endpoints on IP networks.
- Application Programming Interface (API): Sets of protocols, tools, and definitions for building application software. APIs enable different software applications to communicate, allowing for the integration of third-party services into applications.
The Application Layer is crucial in facilitating end-user processes and providing high-level data abstractions, enabling a wide range of network applications and services to operate efficiently across diverse communication systems and networks.
References
- ↑Definition - What does Application Layer Mean?
- ↑What is Application Layer?
- ↑Application Layer Protocols
- ↑Functions of Application Layer
- ↑Application Layer Threats
- ↑Steps to Providing Security at the Application Layer
Further Reading
- Security Think Tank: Three ways to safeguard against application layer vulnerabilities
- Securing the Application Layer


